- Products
- Integrations
- Plans
- Success Stories
- Resources
- Latest WhitepaperUnmasking the Shadows: Invalid Traffic 2024
Learn everything you need to know about Invalid Traffic in 2024 based on our customers’ data. Including a breakdown into marketing channels, industries and much more.
Resources
- Company
- Company
- Blog
What is Invalid Traffic? How to protect yourself from GIVT & SIVT

Oliver Kampmeier
Cybersecurity Content Specialist

What is Invalid Traffic (IVT)?
According to Google’s definition, Invalid Traffic (IVT) is a generic term for all forms of ad impressions or click activity that is not based on the activity of human users with genuine (purchase) interest, but is generated automatically, e.g. by bots. In addition to accidental ad clicks, the term primarily includes all types of non-human traffic (NHT).
Advertisers and publishers are interested in consumers and thus potential customers seeing their ads and being directed by a click to their websites to convert there. Non-human traffic artificially and unnecessarily drives up advertisers’ costs simply because bots click on the ads but cannot become customers.
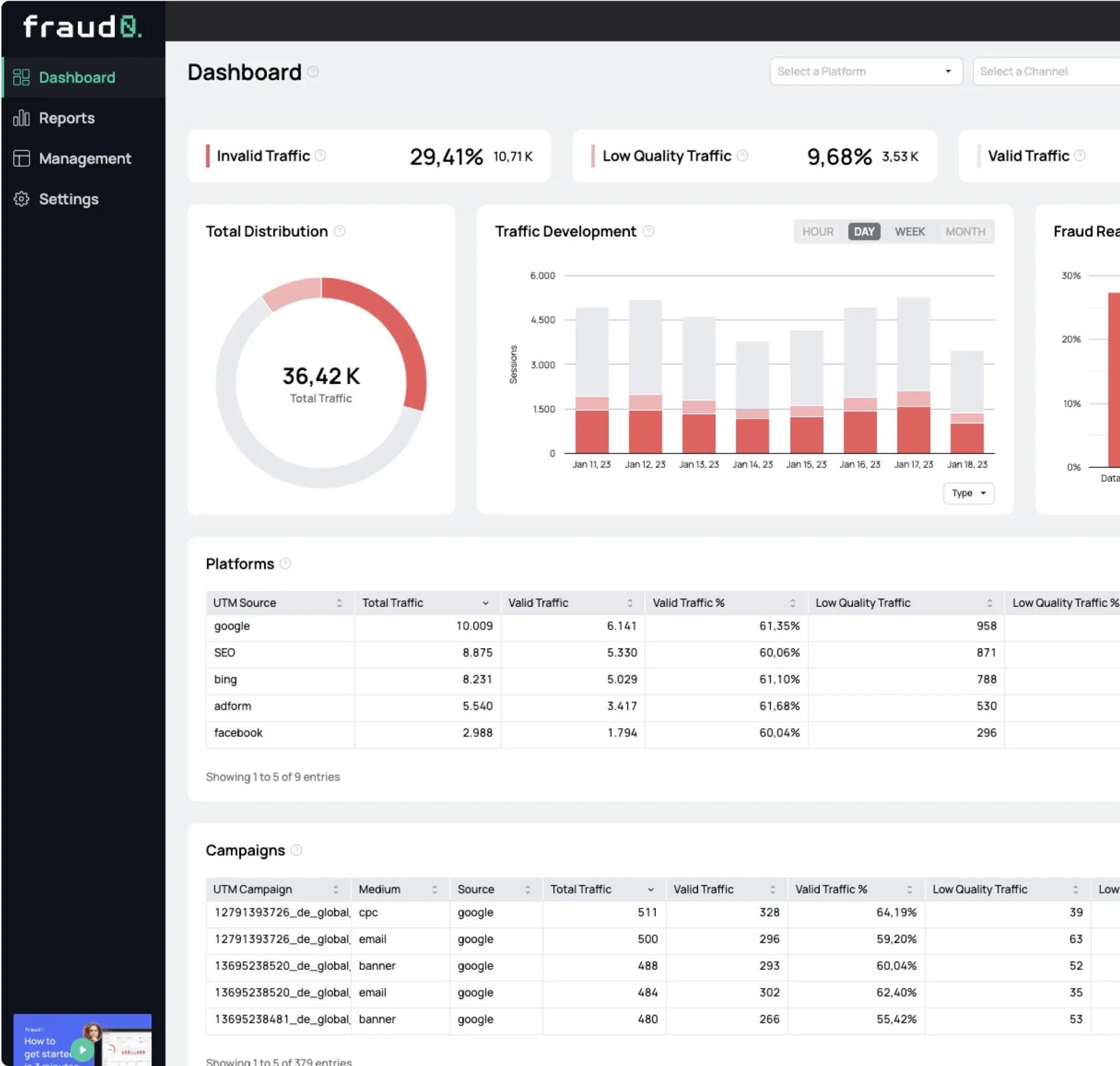
According to our data, around 57% of global online traffic is due to bots and therefore Invalid Traffic. Other estimates range from 42% to 64%. It is difficult to say exactly how high the exact figure is. But one thing should be clear from all the analyses: Bots account for a significant portion of global Internet traffic, around 50%.
What are the different types of Invalid Traffic?
Invalid traffic is not always due to malicious bots and is therefore not necessarily related to fraud. Basically, a distinction must be made between two variants: General Invalid Traffic (GIVT) and Sophisticated Invalid Traffic (SIVT).

General Invalid Traffic (GIVT)
General invalid traffic occurs when “benign” bots such as search engine crawlers access a website. They identify themselves as such and are usually recorded in common bot overview lists (such as the IAB/ABC International Spider and Bots List). Webmasters can thus easily locate GIVT and filter them out in their data.
The different GIVT categories include:
Search engine crawlers
Search engines crawl the Internet using special bots (crawlers) to discover new content and display it in search results. This IVT variant is thus in the interests of website operators.
Search engine crawlers clearly identify themselves as non-human and are easily filterable.
Bots & known crawlers
Known web crawlers self-identify as non-human and can thus be easily identified and filtered out. They are similar to search engine crawlers and are used for research purposes or price comparisons, for example.
Another example are monitoring tools of all kinds: SEO tools (such as Searchmetrics, SEMrush, Ahrefs etc.) or uptime monitoring tools, which keep an eye on the accessibility of servers, are just a few examples of “good” Invalid Traffic that can be easily identified.
Data centers
If the IP address associated with non-human traffic can be traced back to a data center, this is a clear indication of bot traffic. Officially listed data centers, for example, are listed in various bot lists, and the IP addresses are known.
Double and accidental clicks
Duplicate or accidental clicks on ads are also considered GIVT. Both cases are relatively well captured by ad networks, which means advertisers usually do not have to pay money for these clicks.

Sophisticated Invalid Traffic (SIVT)
Traffic based on potentially fraudulent manipulation is to be classified as SIVT. Because it has been manipulated or generated with presumably malicious intent, it does not identify itself as invalid traffic. On the contrary, SIVT actively tries to disguise itself as human traffic using all means at its disposal.
Advertisers lose part of their advertising budget due to SIVT. Malicious bots are often difficult to identify and can cause major problems. Below are some examples of SIVT:
Advanced Bots
Bot developers try to imitate human behavior realistically. For example, bots can accept cookie banners, store cookies, and also interact with a web page in various ways, such as scrolling, mouse movements, filling out forms, etc.
The goal of the fraudsters is to pass the bots off as real users. This way, they can subsequently click on advertisements of their own websites, thereby fraudulently earning advertising revenue.
Hidden ads / ad stacking
Ad stacking is one of the most common forms of ad fraud. Several ads are stacked on top of each other on one ad space. However, only the top ad is visible to the user. One click affects the entire stack and all advertisers pay, even though the hidden ads were never seen by any real user.
Cookie Stuffing
Cookie stuffing is the illegal marking of end devices by cookies. In this form of affiliate fraud, hundreds of cookies are set in the background by the affiliate / website when the page is called up, in order to receive a commission afterwards if the user converts successfully.
It is important to know that cookies are set during cookie stuffing without a user having clicked on a corresponding affiliate or advertising link and thus having expressed an interest in buying.
Learn more about Affiliate Marketing Fraud in our article: What is Affiliate Marketing Fraud
Scraper Bots
Scraper bots, such as content or price scrapers, are used to extract certain information from websites. Often these bots are used by competitors who want to gain an unfair competitive advantage. The extracted data is then used to adjust the pricing of their own offer accordingly, or is intended to save time and money in store design by illegally taking over images and product descriptions.
Auto-reload / Auto-refresh
Without active user interaction, advertising spaces are constantly reloaded and thus generate numerous ad impressions. Auto-reloading or reloading ads is not fundamentally illegal, but each ad must be displayed for a certain amount of time. If the ad space is reloaded too quickly, it may be considered an invalid impression.
Proxy traffic
Proxies and VPNs provide anonymity to fraudsters and make it easier to mask fraudulent traffic. By constantly changing IP addresses, bots are not blocked by common website security mechanisms.
However, VPNs are also used by many real people, which is why not all VPN traffic has to be harmful in general.
Click Farms
It doesn’t always have to be automated bots that are responsible for SIVT. Click Farms are a professionally organized group of workers whose job is to click on ads on the web, share social media posts or post comments. Thus, while real people are responsible for traffic, they have no intention of converting.
More information on click farms is available in our article: What is a Click Farm?
Click fraud by competitors
Clicks on competitors’ ads are primarily used to weaken the competition. Since advertisers pay per click in Google Ads campaigns, for example, frequent clicks by competitors quickly deplete the competitor’s (daily) budget. Once this is used up, the competitor’s ad no longer appears.
Domain Spoofing
In domain spoofing, fraudsters spoof the domain submitted in the ad call to the ad network. The ad network assumes that an ad is being requested for domain A (high-priced website), when in fact domain B (fraudster’s fake website) is requesting the ad.
The goal of domain spoofing is often to get higher click prices for the ads.
DDoS attacks
DDoS attacks (DDoS = Distributed Denial of Service) aim to deliberately overload networks or online services in order to harm companies. Attackers rely on a targeted overload of the IT infrastructure and deliberately cause the inactivity of servers or services.
Manipulated user behavior
This form is particularly common in low-quality or fake apps. Once the app has been installed by a real user, ads are loaded and clicked in the background without the user noticing.
But even during active use of manipulated apps, real users can unknowingly click on ads. These are simply superimposed invisibly over the app, which means that every interaction of the user with the app also represents an interaction with an ad.

Learn everything you need to know about Invalid Traffic in 2024 based on our customers’ data. Including a breakdown into marketing channels, industries and much more.

Damage caused by Invalid Traffic (IVT) to companies
Invalid Traffic is by no means just an annoying side effect for companies. The potential damage is manifold, so the problem should by no means be underestimated.
Although invalid traffic is not fundamentally a criminal act, general invalid traffic (GIVT) can also eat up unnecessary money and place a heavy burden on budgets.
Juniper Research estimates that global damage of $68 billion will be caused by ad fraud in 2022 – a large proportion of which will be caused by invalid traffic. Other experts even assume significantly higher damage amounts.
Damages from IVT to publishers
In addition to the high costs and limited advertising impact for companies, Invalid Traffic also has a negative impact on publishers and has been a growing threat for some time.
Possible consequences are distorted analytics data and thus an incorrect data basis for important business decisions.
Another serious consequence for publishers is the impairment of the value of ad inventory. If advertisers detect Invalid Traffic, they can put publisher websites on a block list. In the worst case, publishers’ accounts may even be blocked if ad networks like Google & Co. detect Invalid Traffic.
The best protection against these problems is therefore to prevent invalid traffic automatically using software.
Damages from IVT to advertisers
The negative consequences of Invalid Traffic for advertisers are usually more serious than for publishers and can be presented in three categories:
Waste of advertising spend
Clicks made by bots (fake clicks) exhaust the advertising budget and do not generate customers. They also simulate human behavior, which leads to distorted remarketing lists (fake remarketing) and thus further downstream waste of the advertising budget. As a result, bots can contaminate audiences and falsify data, making it almost impossible to optimize advertising campaigns in a targeted manner.
Polluted analytics data
Bots simulate a supposedly real browsing history and are now also capable of accepting cookie banners. Distortions of website statistics as well as opt-in rates occur. This website and CMP data leads to a distorted data base.
Polluted Funnel
Forms secured with CAPTCHAs have long been a no-brainer for bots. As a result, fake leads and incorrect data in the CRM are no longer uncommon. The sales team is confronted with unnecessary workload and has to distinguish bots from real users.
Since the consequences of Invalid Traffic for companies are very far-reaching, we have dedicated a separate article to the topic: Impact of Invalid Traffic on your marketing
Detect Invalid Traffic in Analytics Data
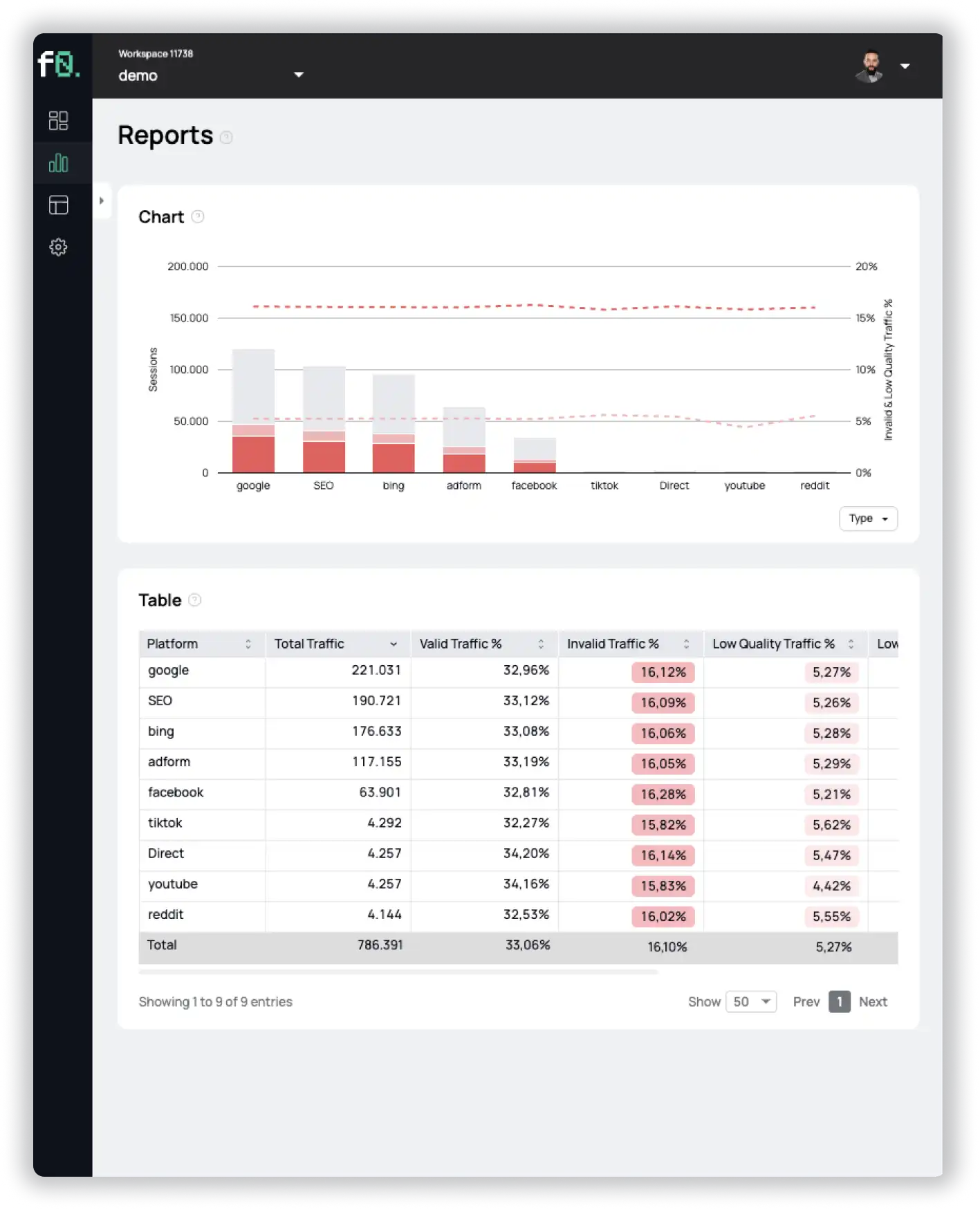
The serious consequences for advertisers can be prevented if invalid traffic is detected and blocked in advance. In many cases, your own Analytics data is already sufficient to identify Invalid Traffic. A close look at the data from Google Analytics or a comparable analysis tool provides initial indications of possible bot activities. Regular analysis of your own Analytics data is therefore an important basis for the fight against IVT.
Invalid Traffic can be identified by the following metrics:
- Session duration: bots leave the website immediately after the click, so the session duration is usually 0 seconds.
- Bounce rate: Humans react differently, but bots are programmed to always do the same thing. A bounce rate of 0% or 100% is a clear indication of bot traffic.
- Unusual locations: Unusual locations are countries that are not targeted as the main market. For example, traffic from developing countries may indicate click farms.
- Unusual traffic patterns: Peaks or outliers and unusual traffic at night can be clear alarm signals.
- Unusual referral traffic: Unknown or unusual referral sources may indicate that ads have been placed on non-public or questionable domains.
If you want to learn more about how to detect Invalid Traffic using your own Analytics data, we recommend our in-depth article on this: How to Detect Bots Using Your Own Analytics Data.
Block Invalid Traffic
If several signals such as high bounce rates, unusual referral traffic, low session duration, etc. show up, this can be a clear sign of Invalid Traffic. However, those affected do not have to accept the damage caused by Invalid Traffic by any means, but the IVT problem should not be underestimated either. It is important to minimize the scope of action of fraudsters and to protect one’s own advertising budget.
Combating IVT is a major challenge; manual measures are time-consuming and cost-intensive; moreover, Invalid Traffic can hardly be blocked with these limited means. Manual interventions are only ever possible reactively after the fact, when the budget has already been wasted. However, the goal must be proactive protection against financial losses, so it is important to block harmful bot traffic reliably right from the start.
For effective impact, bot detection must be active in real time. Collective protection based on different manual and automated measures is recommended. These include, for example:
- Set up IP block lists on advertising channels.
- Manually check publishers and exclude them if necessary
- Restricting campaigns to geolocation
- Regular review of analytics data
- Installing an alert system and reacting as quickly as possible when warning signals occur
For effective protection, software is indispensable that unerringly detects and actively avoids Invalid Traffic.

Conclusion: Protect your advertising budget against IVT
Invalid Traffic is a complex issue and can take many forms. In particular, the fraudulent intentions of SIVT cause billions in damage every year.
The negative consequences of Invalid Traffic for companies are manifold, so a targeted fight is essential. However, the IVT problem can hardly be tackled manually. Effective protection for the advertising budget can only be provided by software that reacts in real time and unerringly detects and combats IVT.
Convince yourself of the effectiveness of modern security measures and take advantage of the free 7-day trial period of fraud0 now.
Frequently Asked Questions about IVT
What is Invalid Traffic?
Invalid Traffic is a generic term for all forms of non-human traffic that cannot generate potential customers. A distinction must be made between General Invalid Traffic (GIVT) and Sophisticated Invalid Traffic (SIVT), as IVT is by no means only due to malicious bots.
What is GIVT?
General Invalid Traffic (GIVT) is common invalid traffic attributable to “benign” bots, such as search engine crawlers, etc. They reveal themselves as non-billing traffic during accesses and are easy to filter out using simple detection solutions.
What is SIVT?
SIVT is traffic based on potentially fraudulent manipulation. The malicious intent causes SIVT to masquerade as human traffic, making it much harder to detect.
How can IVT be blocked?
Manual measures are not effective. Only high-quality software solutions such as fraud0 offer real protection against Invalid Traffic.
How much IVT does a website have?
Based on data analysis, there is evidence that more than half of all online traffic (57%) comes from bots and is therefore automated. Our data shows that about 16% of all clicks on ads are Invalid Traffic.
- Published: December 7, 2022
- Updated: November 28, 2023
1%, 4%, 36%?