- Blog
Methbot – How the King of Fraud made $3 million per day with advertising fraud

On November 10, Aleksandr Zhukov, the “king of fraud,” as he called himself, was sentenced to 10 years in prison and ordered to pay over $3.8 million in restitution:
“[He] was convicted by a federal jury in Brooklyn of four counts of a superseding indictment charging him with wire fraud conspiracy, wire fraud, money laundering conspiracy, and money laundering. The charges arose from Zhukov’s sophisticated scheme to defraud brands, ad platforms and others in the U.S. digital advertising industry out of more than $7 million.” (DOJ)
The Department of Justice said that between September 2014 and December 2016, Aleksandr Zhukov and several co-conspirators carried out the digital advertising fraud through an alleged advertising network Media Methane, hence the name “Methbot” for the scheme.
How the Methbot fraud worked
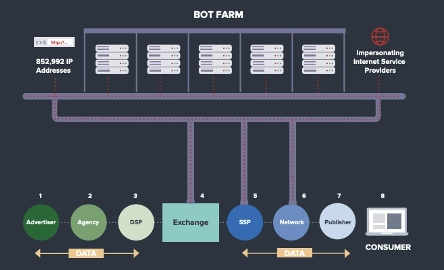
Before we dive deeper into the technical mechanics of how Methbot operated, it is important to understand the scale of the Methbot scheme and why it was one of the biggest advertising frauds of all time.
At its peak, 200 to 400 million video ad views per day were faked by using over 2,000 different servers with over 650,000 residential IP addresses. With a relatively high CPM for video ads, ranging from $3 to $36, it is estimated that the scheme earned its operators $3 to $5 million in ad revenue per day! The Methbot operation spoofed over 6,000 domains with over 250,000 URLs and targeted high-value marketplaces including private marketplaces (PMPs).
In a nutshell Methbot delivered real ads from real advertisers and advertising networks to fake and non-existing users (bots) via fake and spoofed websites. The bots used were very sophiticated, pretending to be real users by visiting the spoofed domains through a fake browser, faking mouse movements, scrolling the page, starting and stopping a video player midway and falsely pretending to be logged in to Facebook (DOJ).
With the overall strategy explained, let us have a look at some more technical mechanisms the Methbot operation used.
Distributed servers
Methbot used over 2,000 physical servers located in data centers in Dallas, Texas, and Amsterdam, the Netherlands. Each server ran multiple instances of the Methbot browser component and a proxy in order to obfuscate the IP address.
Proxy network with lots o residential IP adresses
Ad fraud operated from data centers is usually easy to detect due to various reasons, one being the IP address. Therefore, most ad fraud operations infect private computers through malware. Once infected, the botnet uses the IP address of the infected device and runs fake browser sessions in the background without the victims’ knowledge. This approach entails hard and continuous work, as new computers need to be constantly infected while existing infections are detected and cleaned by anti-malware vendors and other tools.
Methbot’s operators took a different approach: they rented over 650,000 different residential IP addresses with fake registration details and made the bots appear to be real American Internet users coming from legitimate Internet service providers (ISPs) such as Verizon, Comcast, and AT&T.
Sophisticated tech-stack with open source software
The custom software running the Methbot operation used several open source libraries to add the required features.
- js as the underlying JavaScript (JS) runtime environment in order to run JS code.
- tough-cookie to set cookies in the fake sessions while retaining persistent identities like a Facebook login. This was primarily used to achieve higher CPMs, as certain information is considered more valuable to advertisers due to more precise targeting capabilities.
- cheerio in order to parse HTML markup and traversing / manipulating the resulting data structure.
- JWPlayer to request video ads and to programmatically interact with the video player.

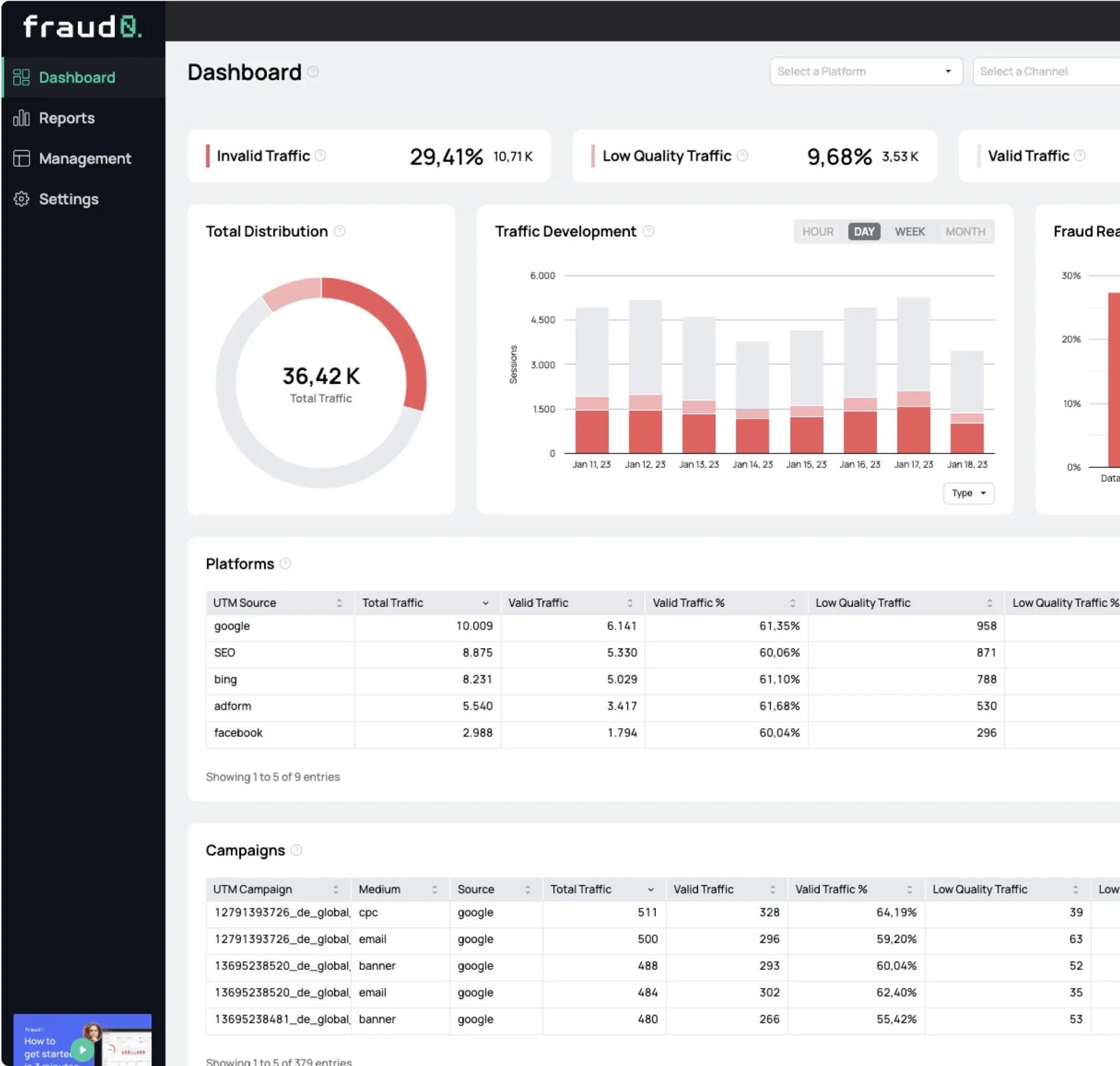
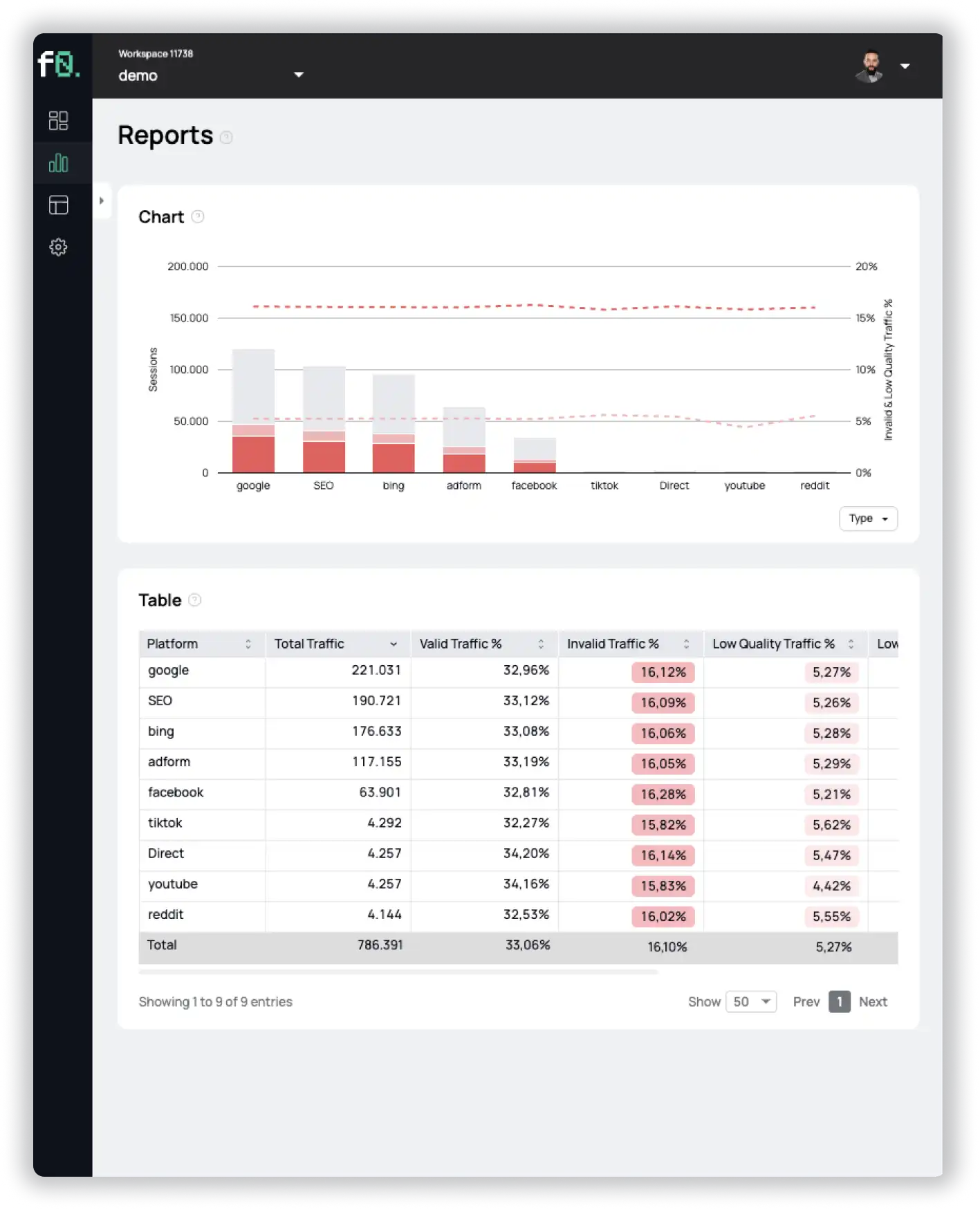
Learn everything you need to know about Invalid Traffic in 2024 based on our customers’ data. Including a breakdown into marketing channels, industries and much more.
Simulating a real browser
On top of proxying the bot traffic through various residential IP addresses, Methbot was able to simulate a real browser in several different ways:
- User agent Methbot was able to fake the user agent string, pretending to be different browsers like Chrome, Firefox, Internet Explorer 11, and even Safari.
- Operating system (OS) Even the operating system was faked, making it look like the requests were coming from Windows and different macOS versions.
- Screen information Information like the browser width and height as well as hardware related information as the color and pixel depth and screen size were faked.
- Browser extensions The creators even thought of adding information coming from different browser extensions.
- Human input simulation Methbot had implemented a random timer that simulated clicks on the website and was also able to randomly simulate clicks on the video player itself to achieve a realistic human behavior and outsmart any click validation logic.
Spoofing premium websites for higher CPMS
In order to get higher CPMs, Methbot spoofed URLs in the call for a video ad, pretending to be a premium publisher website. It did this in 3 simple steps:
- Fake website From a list of premium publishers (e.g. vogue.com, espn.com, foxnews.com) a URL was selected. The system then created a fake website with nothing more than what is needed to run a video ad.
- Make an offer Methbot requests a video ad from an ad network for the fake website using the industry standard Video Ad Serving Template (VAST) protocol with its own unique identifier so that the ad is credited.
- Create views and clicks by fake traffic The video ad is viewed by bots visiting the fake website created in step 1 via the proxied residential IP addresses, looking like real humans interacted with the video ad. Moreover, any code coming from the ad network to fight fraud or check visibility is loaded by Methbot and fed with false signals.
In summary, the creators of Methbot have spared no effort to create the best botnet possible. They even went a step further and reverse-engineered the logic of the most widely used fraud detection vendors in order to fool their systems and not be detected as suspicious traffic.
Methbot – one of the largest and most sophisticated ad fraud schemes of all time
One thing should be very clear by now: Methbot was one of the biggest and most sophisticated ad fraud schemes of all times. Using thousands of servers with hundreds of thousands of different IP addresses and various techniques to circumvent existing anti-fraud systems is not very common, even today.
The dimension of the Methbot scheme was huge, so it is no wonder that Methbot also made our list of the biggest ad fraud cases of the past 5 years.
Protect your business against botnets like Methbot and get an independent opinion on the quality of your ad traffic by signing-up for a free trial with us.
- Published: February 1, 2022
- Updated: November 28, 2023
1%, 4%, 36%?